What Is The Main Purpose Of Encryption
Encryption authentication user Encryption symmetric types decryption data key ico asymmetric using Encryption asymmetric does work data example works decryption use algorithms keys plaintext changes
What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights
Encryption symmetric occurred load Encryption cryptography basics springboard Asymmetric encryption keys security generated two understand
Encoding vs encryption
Cryptography, encryption, hash functions and digital signatureEncryption cyberhoot mezquita ty Best secure instant messaging solutions for enterprise businessWhat is asymmetric encryption?.
Encryption opacity css mime proofpoint secure multipurpose extensions message sending importanceCryptography basics: ins and outs of encryption Encryption integrity confidentiality repudiation authentication nonEncryption cryptography asymmetric symmetric basically consists types second two first.

What is cryptography?
What types of encryption are there?Encryption explained messaging encrypted instant device does bitcoin cyberwarfare pouring malicious actions ged cybersecurity Encryption authentication userEncryption encoding.
Cryptography encryption hash signature digital functionsWhat is asymmetric encryption & how does it work? What is encryption?Advanced encryption package 2017 6.06.

Symmetric encryption: definition & example
Encryption advanced package app windows .
.


What is Cryptography? - UseMyNotes

What Is Asymmetric Encryption? - DZone

Best Secure Instant Messaging Solutions for Enterprise Business

DigiBrains - Encryption

Cryptography, Encryption, Hash Functions and Digital Signature

Encoding vs Encryption - App Security Mantra

Cryptography Basics: Ins and Outs of Encryption | Springboard Blog

DigiBrains - Encryption
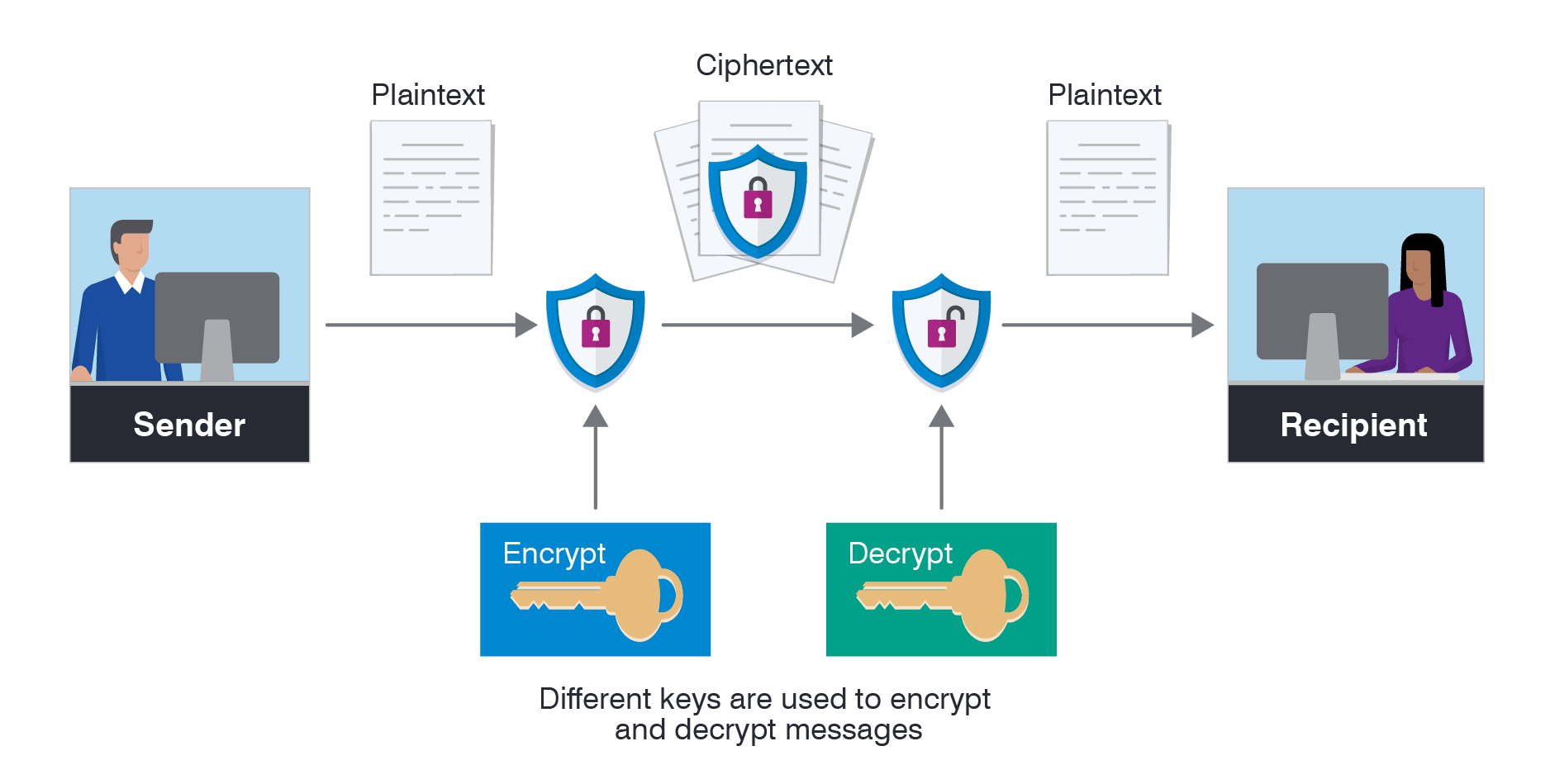
What Is Encryption? - Definition, Types & More | Proofpoint US
